Creating a Backdoor Login Account
It explains how to create admin accounts for end-users who also want to have regular RSpace user accounts.
Before starting
- Have a working RSpace, 1.69.36 or later, with SSO login enabled and working.
- Obtain a list of usernames of users that will administer the system.
- Follow the flowchart in Setting up multiple RSpace accounts with the same SSO identity to see if this document is actually relevant for you. If you just want to create a new sysadmin user, and that user will just do admin work, and not want to use RSpace ELN as a researcher, then this document can be ignored.
- If you or one of your users plans to act as both a user (or PI) in RSpace, AND ALSO a Sysadmin or Community admin, it is important to use the appropriate account to perform tasks related to those different roles. Do not add production data when logged in as a Sysadmin, or Community Admin, do not add Admins to any LabGroups, and do not try to use Sysadmin account to fill the PI or standard user role.
- Know login credentials for the
sysadmin1account. - Have access to RSpace server to be able to configure and restart it.
What will happen?
After completing the steps below, an RSpace user will be able to use RSpace both with a user account and an admin account. They will authenticate to RSpace using SSO credentials, which will give them access to their regular PI/user account in RSpace. They will then be able to authenticate as an 'internal admin' user to perform administrative actions in RSpace.
Steps
1. Setting up RSpace to enable creation of extra admin accounts
In deployment.properties, set:
deployment.sso.backdoorUserCreation.enabled=true
deployment.standalone=true
and restart RSpace.
2. Create new backdoor sysadmin login accounts
Login as 'sysadmin1' (RSpace's internal, pre-created sysadmin user) and create the new sysadmin accounts:
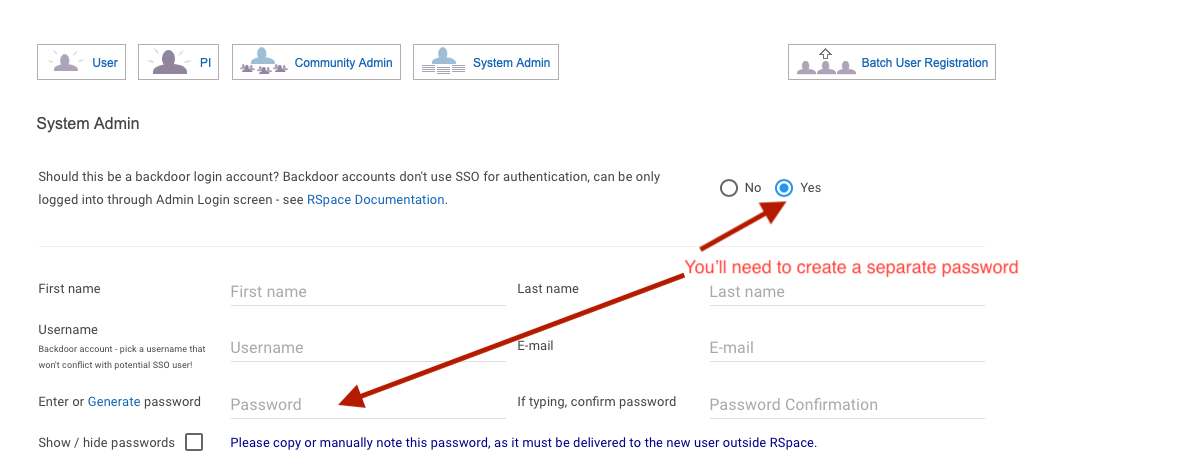
You'll need to set a password for these accounts.
- The username can be anything you like, but it shouldn't be an SSO username, to avoid conflicts with existing or future usernames.
- Please use a different password from your SSO password.
- These backdoor accounts aren't tied to any particular user's SSO account.
- The second account will need a separaet and unique email address, even if you have to make up a dummy address that goes nowhere.
- These accounts don't bypass SSO authentication and can't be accessed directly. For security reasons, these accounts can only be accessed by a user who has already authenticated to RSpace using SSO authentication.
3. Activating the adminLogin
In deployment.properties, configure RSpace to start using SSO authentication, and enable internal admin login:
deployment.standalone=false
deployment.sso.adminLogin.enabled=true
If you don't want any existing sysadmin users to create new backdoor login accounts in future, set:
deployment.sso.backdoorUserCreation.enabled=false
Restart RSpace.
4. Testing the account
- Login to RSpace using your existing SSO credentials.
- In your browser, navigate to the special backdoor login page:
[your server URL]/adminLogin
Login as the backdoor admin using the credentials you supplied in step 2. - You should now be logged in as that admin user. You will see a special banner reminding you that you are logged in as an backdoor user.
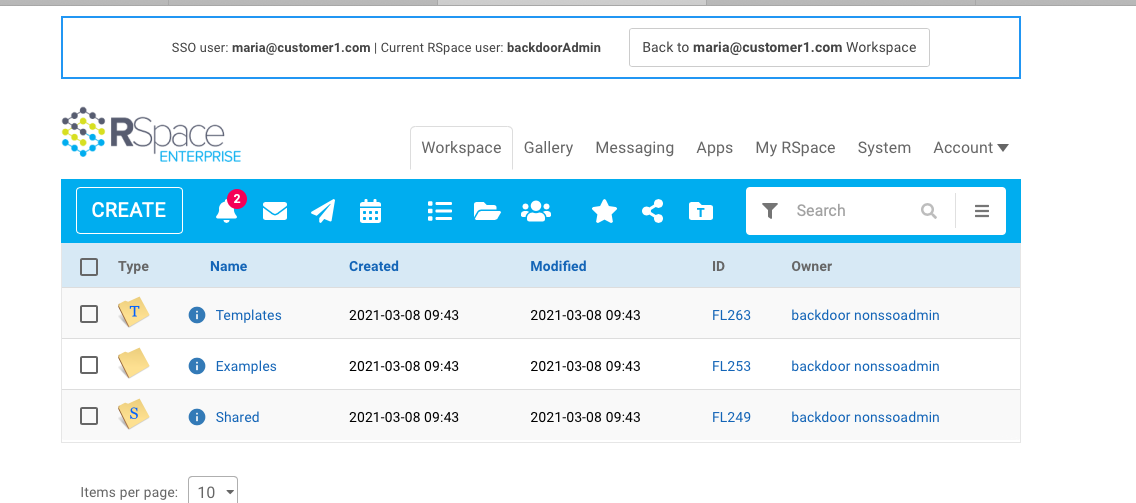
- Logout
5. Final steps
Notify the user(s) who you want to use this backdoor admin account. If users can self-signup (see Setting up SingleSignOn authentication) then they can signup and use RSpace directly. If not, and they don't have an existing user/PI account, then you'll need to create regular user/PI accounts for them.